How trojan works top
How trojan works top, Smart phone malware The six worst offenders top
$74.00
SAVE 50% OFF
$37.00
$0 today, followed by 3 monthly payments of $12.33, interest free. Read More
How trojan works top
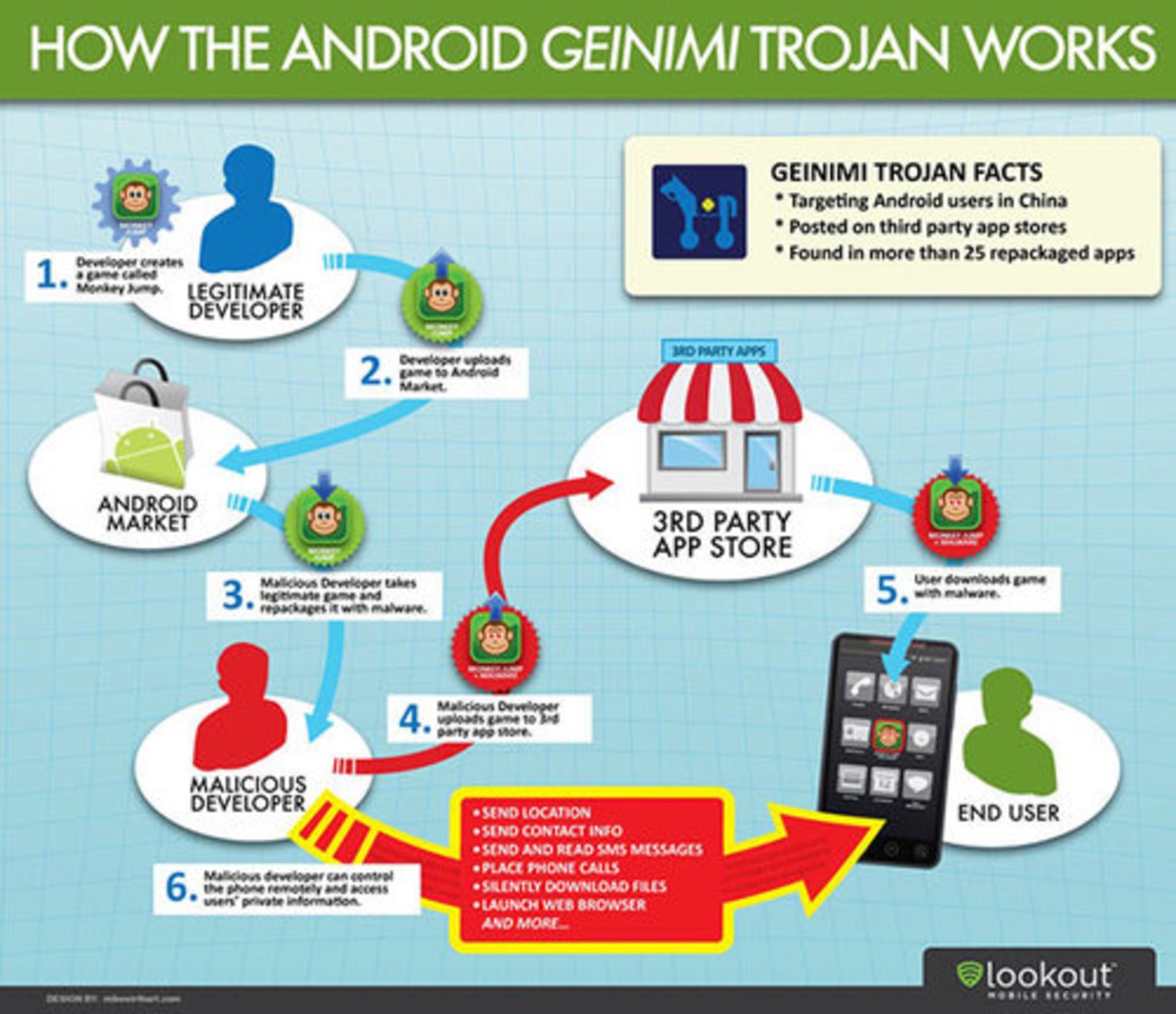
Smart phone malware The six worst offenders
What is Trojan Horse Virus Protect Yourself Against Trojan Viruses
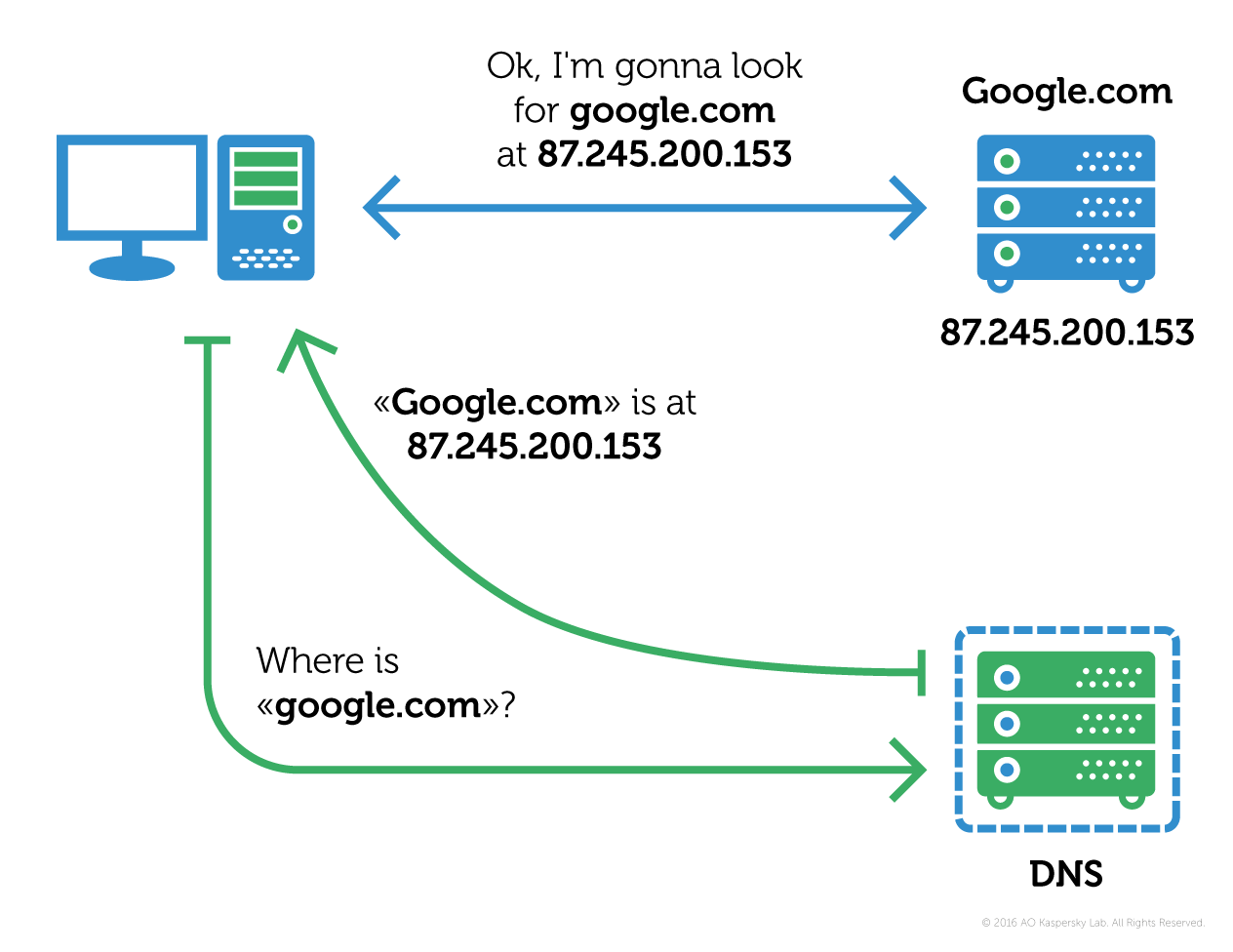
The Switcher Trojan hacks Wi Fi routers switches DNS Kaspersky
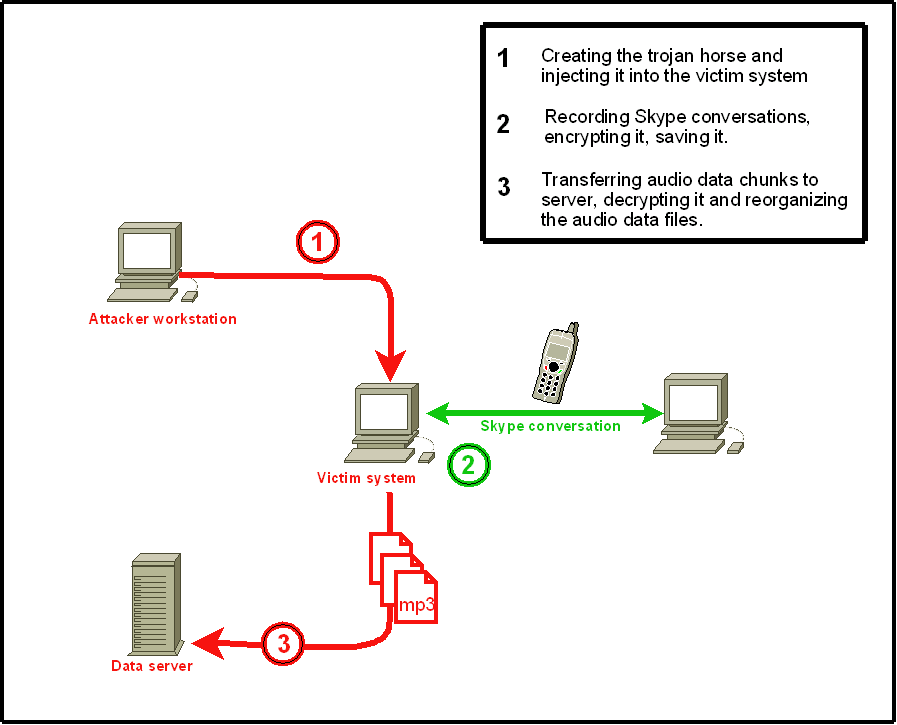
Source code for Skype eavesdropping trojan in the wild ZDNET
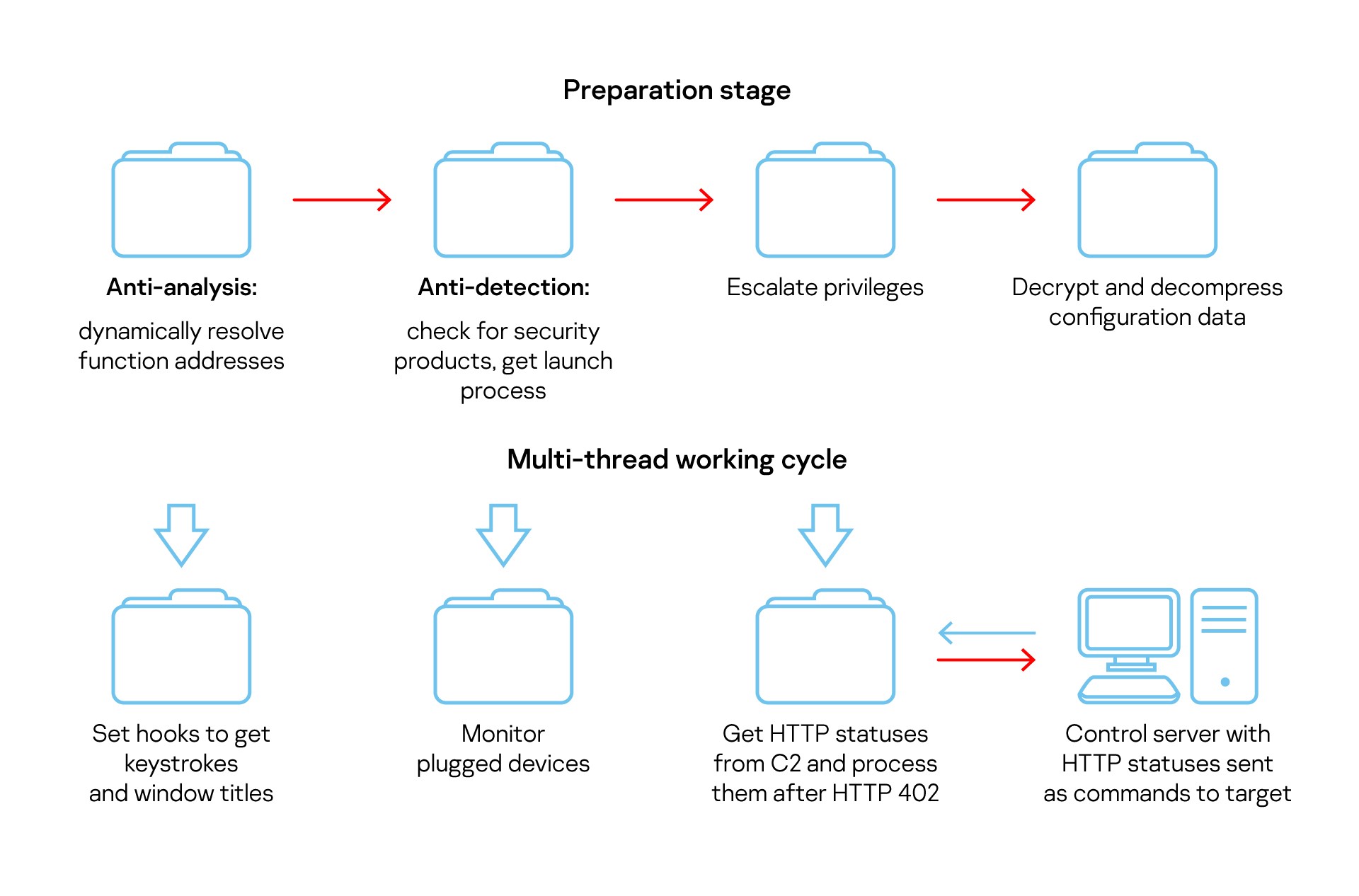
COMpfun authors spoof visa application with HTTP status based
Zeus malware Wikipedia
Description
Product Name: How trojan works top
What is a Trojan Virus Trojan Horse Malware Imperva top, What is a Trojan Horse Virus Types Prevention in 2024 top, Trojan Malware Understanding the Rising Threat of Cybercrime top, What is Proxy Trojan GeeksforGeeks top, What Is a Trojan a Virus or Malware How Does It Work Avast top, What Are Trojans How Can You Protect Yourself top, What is a Trojan Horse How Trojan Horse Malware Works top, What is Remote Access Trojan RAT Detection and Removal top, What is Trojan Horse Attack . Series 2 Chapter 9 by Anuja Pawar top, A New Banking Trojan on the Rise TOITOIN Banking Trojan top, Glimpsing inside the trojan horse An insider analysis of Emotet top, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet top, What is Remote Access Trojan RAT Malware CYBERVIE top, Trojan attack PPT top, Smart phone malware The six worst offenders top, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses top, The Switcher Trojan hacks Wi Fi routers switches DNS Kaspersky top, Source code for Skype eavesdropping trojan in the wild ZDNET top, COMpfun authors spoof visa application with HTTP status based top, Zeus malware Wikipedia top, Trojan Horse Virus and Hacking PPT top, Banking malware Unveiling the Secrets of the Banker Trojan top, How DNS Changer Trojans Direct Users to Threats Threat Encyclopedia top, Trojan Virus Gooligan Infects More Than a Million Google top, What Is a Trojan a Virus or Malware How Does It Work Avast top, What are Remote Access Trojans RATs How these attacks can be top, What is Antivirus Software Definition from TechTarget top, What are Remote Access Trojans RATs How these attacks can be top, Hardware Trojan attacks in different forms a combinational and top, General structure of a hardware Trojan in a design. Download top, What is a Trojan Horse and How Does It Work YouTube top, The inserted Trojans in the circuit II. RELATED WORKS Different top, how does Trojan horse works Explain Brainly.in top, The Remote Access Trojan wearedevs discord thirstymag top, How to prevent a trojan horse or trojan The Security Buddy top.
What is a Trojan Virus Trojan Horse Malware Imperva top, What is a Trojan Horse Virus Types Prevention in 2024 top, Trojan Malware Understanding the Rising Threat of Cybercrime top, What is Proxy Trojan GeeksforGeeks top, What Is a Trojan a Virus or Malware How Does It Work Avast top, What Are Trojans How Can You Protect Yourself top, What is a Trojan Horse How Trojan Horse Malware Works top, What is Remote Access Trojan RAT Detection and Removal top, What is Trojan Horse Attack . Series 2 Chapter 9 by Anuja Pawar top, A New Banking Trojan on the Rise TOITOIN Banking Trojan top, Glimpsing inside the trojan horse An insider analysis of Emotet top, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet top, What is Remote Access Trojan RAT Malware CYBERVIE top, Trojan attack PPT top, Smart phone malware The six worst offenders top, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses top, The Switcher Trojan hacks Wi Fi routers switches DNS Kaspersky top, Source code for Skype eavesdropping trojan in the wild ZDNET top, COMpfun authors spoof visa application with HTTP status based top, Zeus malware Wikipedia top, Trojan Horse Virus and Hacking PPT top, Banking malware Unveiling the Secrets of the Banker Trojan top, How DNS Changer Trojans Direct Users to Threats Threat Encyclopedia top, Trojan Virus Gooligan Infects More Than a Million Google top, What Is a Trojan a Virus or Malware How Does It Work Avast top, What are Remote Access Trojans RATs How these attacks can be top, What is Antivirus Software Definition from TechTarget top, What are Remote Access Trojans RATs How these attacks can be top, Hardware Trojan attacks in different forms a combinational and top, General structure of a hardware Trojan in a design. Download top, What is a Trojan Horse and How Does It Work YouTube top, The inserted Trojans in the circuit II. RELATED WORKS Different top, how does Trojan horse works Explain Brainly.in top, The Remote Access Trojan wearedevs discord thirstymag top, How to prevent a trojan horse or trojan The Security Buddy top.