Threat hunting tools top
Threat hunting tools top, Best Threat Hunting Tools Top 5 Open Source Tools top
$84.00
SAVE 50% OFF
$42.00
$0 today, followed by 3 monthly payments of $14.00, interest free. Read More
Threat hunting tools top
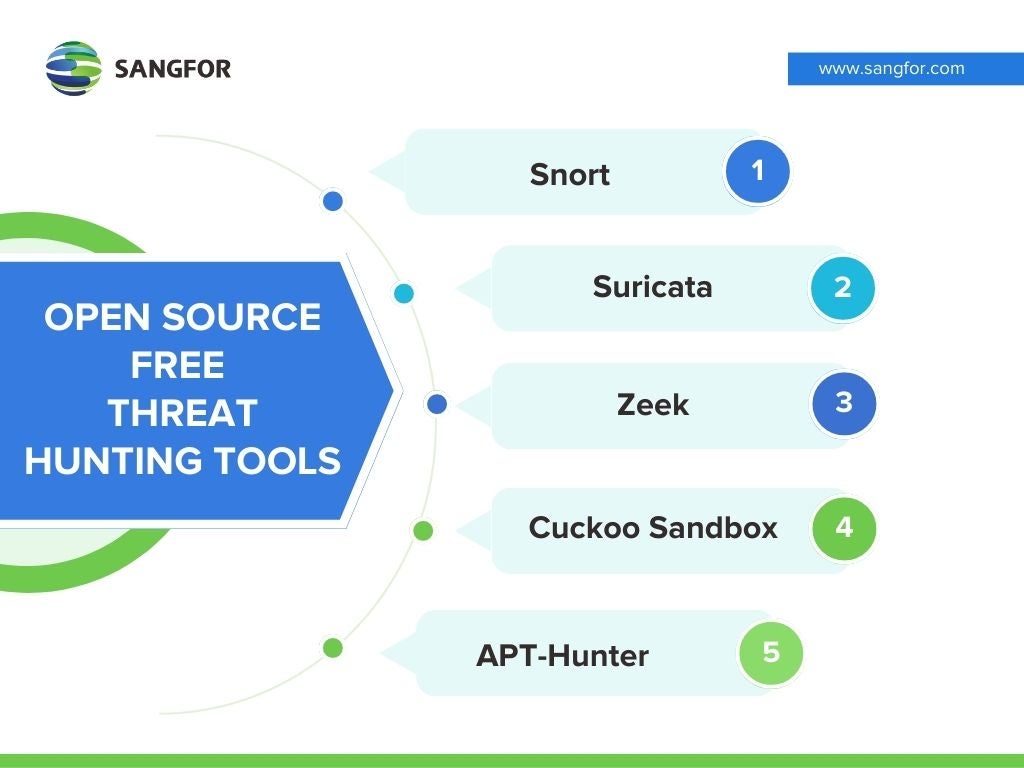
Best Threat Hunting Tools Top 5 Open Source Tools
Free and Open Source Threat Hunting Tools. The Best Options for
10 Best Cyber Threat Hunting Tools for 2024
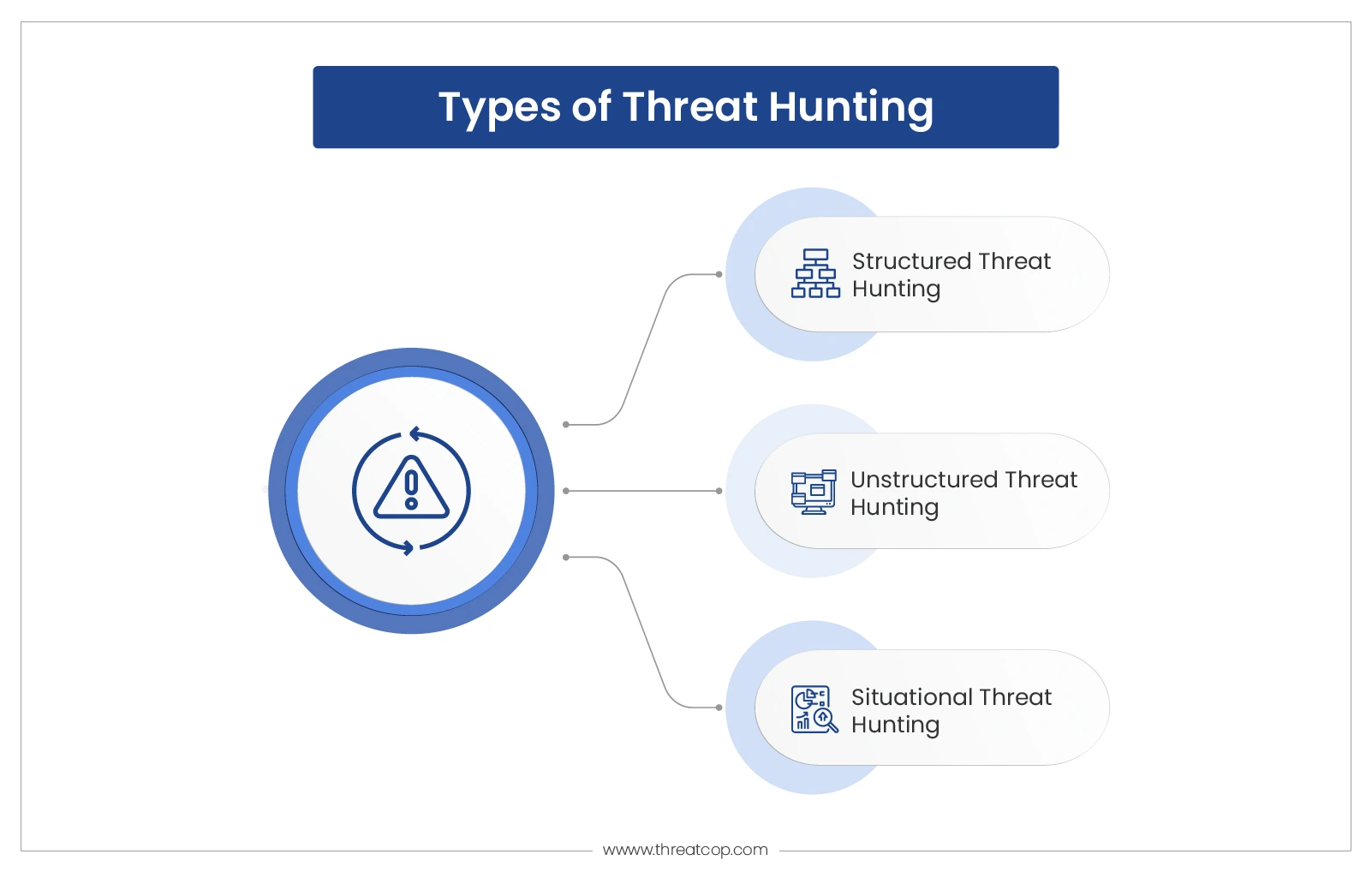
Threat Hunting What is it and How is it Done ThreatCop
25 Essential Threat Hunting Tools for Your Arsenal in 2024
5 Commercial Threat Hunting Platforms That Can Provide Great Value
Description
Product Name: Threat hunting tools top
Threat Hunting Tools Top 3 Types of Threat Hunting Tools with top, InfoSec s Top 10 Threat Hunting Tools for 2023 Skyhawk top, What is Threat Hunting Threat Hunting Types and Techniques top, 25 Essential Threat Hunting Tools for Your Arsenal in 2024 top, Best Threat Hunting Tools Top 5 Open Source Tools top, 10 Best Threat Hunting Tools for 2024 Paid Free Trials top, A first look at threat intelligence and threat hunting tools top, Top 9 Threat Hunting Tools for 2023 CybeReady top, Threat Hunting Tools Top 3 Types of Threat Hunting Tools with top, Leveraging Threat Hunting Tools to Improve Threat Detection Response top, Threat Hunting Methodologies Tools and Tips top, Threat Hunting Tools Our Recommendations SOC Prime top, What is Cyber Threat Hunting Proactive Guide CrowdStrike top, Threat Hunting Techniques A Quick Guide top, Best Threat Hunting Tools Top 5 Open Source Tools top, Free and Open Source Threat Hunting Tools. The Best Options for top, 10 Best Cyber Threat Hunting Tools for 2024 top, Threat Hunting What is it and How is it Done ThreatCop top, 25 Essential Threat Hunting Tools for Your Arsenal in 2024 top, 5 Commercial Threat Hunting Platforms That Can Provide Great Value top, 4 types of cyber threat hunting tools SISA Blog top, Threat Hunting Process Methodologies Tools And Tips top, Cyber Threat Hunting What it is Methodologies Types and Examples top, 20 Best Threat Hunting Tools in 2024 Cyber Security News top, Cyber Threat Hunting PowerPoint Template PPT Slides top, Threat Hunting Process Methodologies Tools And Tips top, Cyber Threat Hunting 101 Guide Methods Tools Techniques top, Python Threat Hunting Tools Part 8 Parsing JSON Kraven Security top, What is Cyber Threat Hunting Proactive Guide CrowdStrike top, What are Threat Hunting Tools SOCRadar Cyber Intelligence Inc top, The impact of threat hunting on your security operations Help top, What is threat hunting CyberProof top, Top Threat Hunting Tools for 2023 Flare top, Cyber Threat Hunting Program With Process And Tools Presentation top, Security Orchestration Use Case Automating Threat Hunting Palo top.
Threat Hunting Tools Top 3 Types of Threat Hunting Tools with top, InfoSec s Top 10 Threat Hunting Tools for 2023 Skyhawk top, What is Threat Hunting Threat Hunting Types and Techniques top, 25 Essential Threat Hunting Tools for Your Arsenal in 2024 top, Best Threat Hunting Tools Top 5 Open Source Tools top, 10 Best Threat Hunting Tools for 2024 Paid Free Trials top, A first look at threat intelligence and threat hunting tools top, Top 9 Threat Hunting Tools for 2023 CybeReady top, Threat Hunting Tools Top 3 Types of Threat Hunting Tools with top, Leveraging Threat Hunting Tools to Improve Threat Detection Response top, Threat Hunting Methodologies Tools and Tips top, Threat Hunting Tools Our Recommendations SOC Prime top, What is Cyber Threat Hunting Proactive Guide CrowdStrike top, Threat Hunting Techniques A Quick Guide top, Best Threat Hunting Tools Top 5 Open Source Tools top, Free and Open Source Threat Hunting Tools. The Best Options for top, 10 Best Cyber Threat Hunting Tools for 2024 top, Threat Hunting What is it and How is it Done ThreatCop top, 25 Essential Threat Hunting Tools for Your Arsenal in 2024 top, 5 Commercial Threat Hunting Platforms That Can Provide Great Value top, 4 types of cyber threat hunting tools SISA Blog top, Threat Hunting Process Methodologies Tools And Tips top, Cyber Threat Hunting What it is Methodologies Types and Examples top, 20 Best Threat Hunting Tools in 2024 Cyber Security News top, Cyber Threat Hunting PowerPoint Template PPT Slides top, Threat Hunting Process Methodologies Tools And Tips top, Cyber Threat Hunting 101 Guide Methods Tools Techniques top, Python Threat Hunting Tools Part 8 Parsing JSON Kraven Security top, What is Cyber Threat Hunting Proactive Guide CrowdStrike top, What are Threat Hunting Tools SOCRadar Cyber Intelligence Inc top, The impact of threat hunting on your security operations Help top, What is threat hunting CyberProof top, Top Threat Hunting Tools for 2023 Flare top, Cyber Threat Hunting Program With Process And Tools Presentation top, Security Orchestration Use Case Automating Threat Hunting Palo top.